Sunil Bakshi worked with State Bank of India in IT implementation and operations for 25 years. Later he worked with the Enterprise Risk Services group of Deloitte Touché Tohmatsu India Private Limited, Mumbai and Wipro consulting services for audit and consulting in security and governance. Sunil was CISO of National Stock Exchange and later visiting faculty with National Institute of Bank Management (NIBM). Currently he is a freelance consultant and trainer in IT governance, Risk Management, IS Audit, Data Privacy and Information Security. Sunil is a senior life Member of the Computer Society of India and is a patron of the Pune chapter. He was previously Chairman of the Pune chapter. Sunil is also a member of ISACA and was founder and past president of the ISACA Pune chapter.
The high-profile attack on SolarWinds underlined the importance of managing security in the supply chain. Suppliers are an essential component of any organization’s success, since then the organization can focus on its niche skills and core business activities. Every business depends on suppliers and thus forming a supply chain. Most organizations have a robust security program that helps them in preventing and/or detecting attacks in time, which prompts the targeted attacker to focus on suppliers of the organization. Tim Brown, the CISO of SolarWinds, expressed in an interview with ISACA Board Director Rob Clyde, “I ran a good program. But my program was not sophisticated enough to combat the Russian SVR. It just wasn’t. Was I doing OK? Yes.” In other words, even when you have sophisticated protection, the motivated attacker will find a way to attack you since organizations cannot have unlimited budget for security. Any organization generally deals with multiple suppliers/service providers, which means there are multiple options for an attacker to focus on if they wish to target your organization.
The reason for this deliberation is the results of ISACA’s recent Supply Chain Security Gaps 2022 survey. The research shows that significant improvements to supply chain governance are required. Some that especially affect security are:
- Supplier assessment process does not include cybersecurity and privacy assessments.
- Absence of incident response plans with suppliers in case of a cybersecurity event.
- Almost half responded that they do not perform vulnerability scanning and penetration testing on the supply chain.
- Many agreed that risk assessments do not include supply chain risk assessments specifically for devices using artificial intelligence (AI).
- A majority say their organization’s supply chain needs better governance than what is currently in place.
What can we do to ensure appropriate security measures for the supply chain so that attacks like SolarWinds can be mitigated? Here are a few considerations:
- Know your suppliers (supply chain governance): The first step in security is to know what we are protecting. Therefore, it is necessary to have complete visibility of all supply chains. In order to achieve that there needs to be a centralized inventory of suppliers prioritized based on the organization’s dependency on them. Organizations should establish a centralized steering committee at the board or senior management level that will oversee the entire supply chain. (Refer to Figure 1 below). The major functions of this steering committee are:
- To maintain inventory of all suppliers and their relationships based on the organization’s dependency for services and products. When the dependency is extensive, the impact of a security breach can be huge.
- Risk management and monitoring supplier-related risk. Monitoring gives early warning of materializing risk.
- Contract and compliance management covers the clauses in contract to ensure compliance with an organization’s security requirements and compliance monitoring. The contract also may cover the processes deployed by the supplier to ensure their supplier’s security monitoring.
- Supplier’s human resource management, particularly those human resources working for organization. If they are the weakest link, human resources can be a security risk.
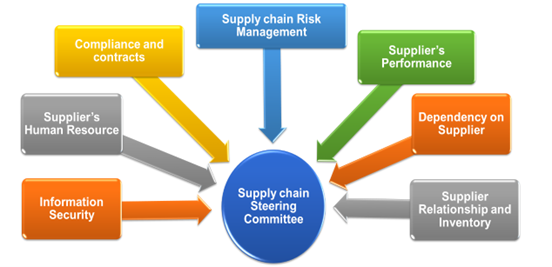
- Monitoring security compliance by the supplier, periodic audits and vulnerability assessment report monitoring.
- Monitoring supplier’s performance as per Service Level Agreement (SLA).
- Security monitoring: Although suppliers are managed through contracts and SLAs, it is essential to ensure that the contract includes the necessary clause for periodic audit and sharing vulnerability assessment and penetration test (VAPT) reports. Ideally an organization should conduct both internal VAPT test and validate the findings with an independent VAPT test performed by a good external agency. Any digital communication between the organization and supplier should be treated as external communication and appropriate controls should be in place.
- Incident management and business continuity: Organization should be aware of the supplier’s incident management process and business continuity plan (BCP) and align them so that interruption at the supplier’s operation may not impact the organization. Wherever possible, joint testing for BCP may be organized to close the gaps, if any. The expectations about the time gap between the incident and notification helps an organization in taking protective steps and minimizing impact. It would be appropriate to state that the contract signed should include joint testing of BCP at least once a year.
- Include in contract appropriate clauses to disclosures about technology being used: The organization should be aware about the technology used by the supplier, particularly open source, and specify the procedural and technical control expectations. This is particularly important when the communication is automated and seamless without intervention (for example, automated patch downloads and updating, sharing of data when processed, etc.) It is also important that the organization be aware of the developments in the technology used by the suppliers and the impact it could have on the organization.
- Determining trust levels: Although having trusted business partners or suppliers helps in reducing controls investments, it is always better to adopt the approach ‘trust but verify’. This also applies to the suppliers of the supplier, and organizations should confirm that their suppliers’ security levels are acceptable.
ISACA has done lot of research in this area and there are many resources on the ISACA website addressing the supply chain issues, including a “How to Manage Supply Chain Risk” e-book and a white paper on supply chain resilience and continuity. There have been many discussions about supply chain security after the SolarWinds attack. Many have predicted that there will be more supply chain attacks in the future. However, prudent measures like strengthening supply chain governance, and monitoring of suppliers’ security and performance need to be considered while entering into contracts with the suppliers.


